Finally, a powerful CRM—made simple.
Attio is the AI-native CRM built to scale your company from seed stage to category leader. Powerful, flexible, and intuitive to use, Attio is the CRM for the next-generation of teams.
Sync your email and calendar, and Attio instantly builds your CRM—enriching every company, contact, and interaction with actionable insights in seconds.
With Attio, AI isn’t just a feature—it’s the foundation.
Instantly find and route leads with research agents
Get real-time AI insights during customer conversations
Build AI automations for your most complex workflows
Join fast growing teams like Flatfile, Replicate, Modal, and more.
Hope you didn’t think we were dropping a newsletter over the 4th—America’s birthday deserves a proper cocktail and a boat. But now that we’re back and (barely) recovered, it’s time to talk about one of the most under-the-radar threats still stealing millions…
🧠 What Is Address Poisoning?
It’s one of crypto’s most clever scams—you do everything right, but still end up sending funds to a scammer. No exploit. No hack. Just manipulation of your memory and your clipboard.
Address poisoning is when a scammer:
Sends a tiny transaction from an address that looks nearly identical to yours or a trusted one
Tricks you into copying the fake address from your history next time you send funds
And steals your assets when you don’t double-check
These aren’t brute-force attacks—they’re sleight of hand. And they’ve already caused over $83 million in confirmed losses across Ethereum, Solana, BNB Chain, and beyond.
🔬 How It Works — Insert the infographic here:
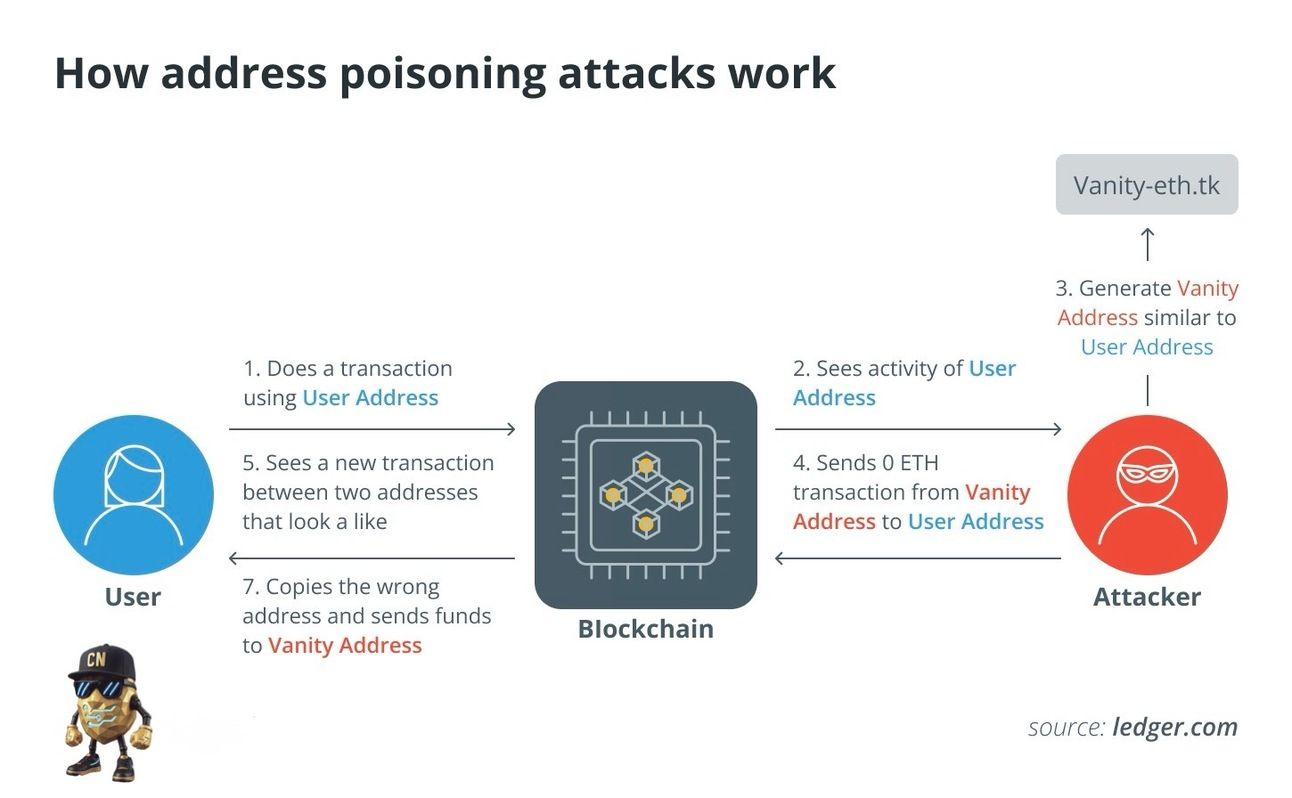
This perfectly explains how scammers:
Track your wallet activity
Create a “vanity address” that looks similar to yours
Send a 0 ETH transfer so it shows up in your transaction history
Wait for you to copy the wrong address next time you transact
All it takes is one careless copy-paste, and your funds are gone.
🧪 Common Techniques
The poison comes in many forms:
Zero-value transfers: Appear in your wallet history, look legit
Fake QR codes: Printed or shared visually to redirect funds
Smart contract spoofing: Malicious contracts that reroute funds
Clipboard malware: Replaces copied addresses with attacker’s
Phishing + Sybil attacks: Fake websites or networks to confuse
These tricks prey on humans, not code.
⚠️ Real World Examples
$2.6M USDT stolen (May 2025): A trader lost millions in two consecutive scams via zero-value transfers. No exploit—just trickery.
$68M WBTC loss (May 2024): One of the largest ever, a trader was tricked into sending 1,155 WBTC to a “lookalike” address.
Vaulta (EOS) attack (March 2025): Attackers spoofed exchange wallets like Binance/OKX to bait users during EOS’ rebrand.
💡Did You Know? Over 270 million zero-value transfer attempts have been logged. It’s not a niche issue—it’s happening constantly.
🔐 How to Stay Safe
Rotate addresses often (use HD wallets)
Use hardware or multisig wallets
Never reuse addresses for receipts
Double check the ENTIRE address before sending—not just first/last 4 digits
Whitelist trusted wallets in apps that allow it
Don’t trust transaction history blindly
Avoid copy-pasting directly from blockchain explorers
Use anti-poisoning tools (like Trugard, Webacy, or Blockfence browser extensions)
🧭 Final Take
Crypto wallets are like digital vaults—but the weakness is always you, not the vault. Address poisoning works because it’s invisible until it’s too late. No malicious link. No shady project. Just one bad copy-paste and it’s game over.
In a world obsessed with airdrops and trading edge, basic wallet hygiene is still the most underrated alpha.
Stay sharp. Stay skeptical. And maybe… don’t send six figures from your phone at the bar.
-Cole



